Protect your SAAS
from fake users with our smart KYC
Automatically detect and prevent fraud with our AI-powered identity verification widget.
Stop fake accounts and protect your revenue with intelligent triggers.
No credit card required.
Customers register to your platform
Our widget will automatically check..
AI-powered fraud detection
Our advanced AI algorithm automatically detects fraudulent behavior and triggers KYC verification when suspicious activity is detected
Fingerprint & IP tracking
Detect duplicate registrations and VPN/proxy usage with unique fingerprint IDs and IP address monitoring
Custom trigger rules
Set up automated KYC triggers based on country, email patterns, temporary mailboxes, and custom business rules
Bot & automation detection
Identify and block automated bots and suspicious user behavior patterns to prevent fraud and abuse
User is a real user, no action needed
User is suspicious, KYC is requested
User is now verified
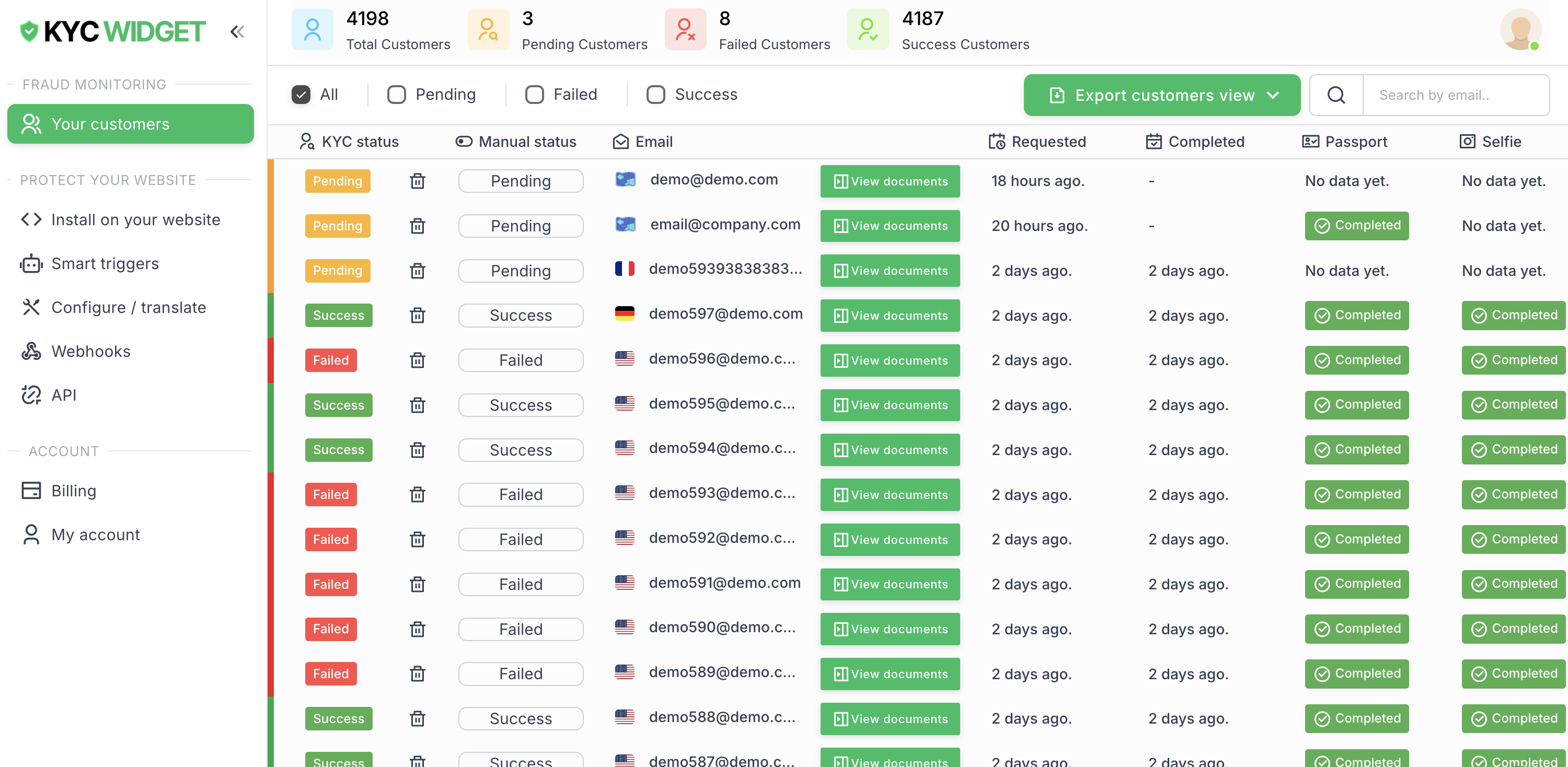
Customer Management
Manage your customers
Customer Dashboard
View all registered customers, track their KYC progress, and manage verification status in real-time.
Webhook Integration
Receive instant notifications when customers complete or fail identity verification.
API Access
Retrieve customer data programmatically and integrate verification results into your systems.
Verification Reports
Detailed reports on verification attempts, success rates, and fraud detection analytics.
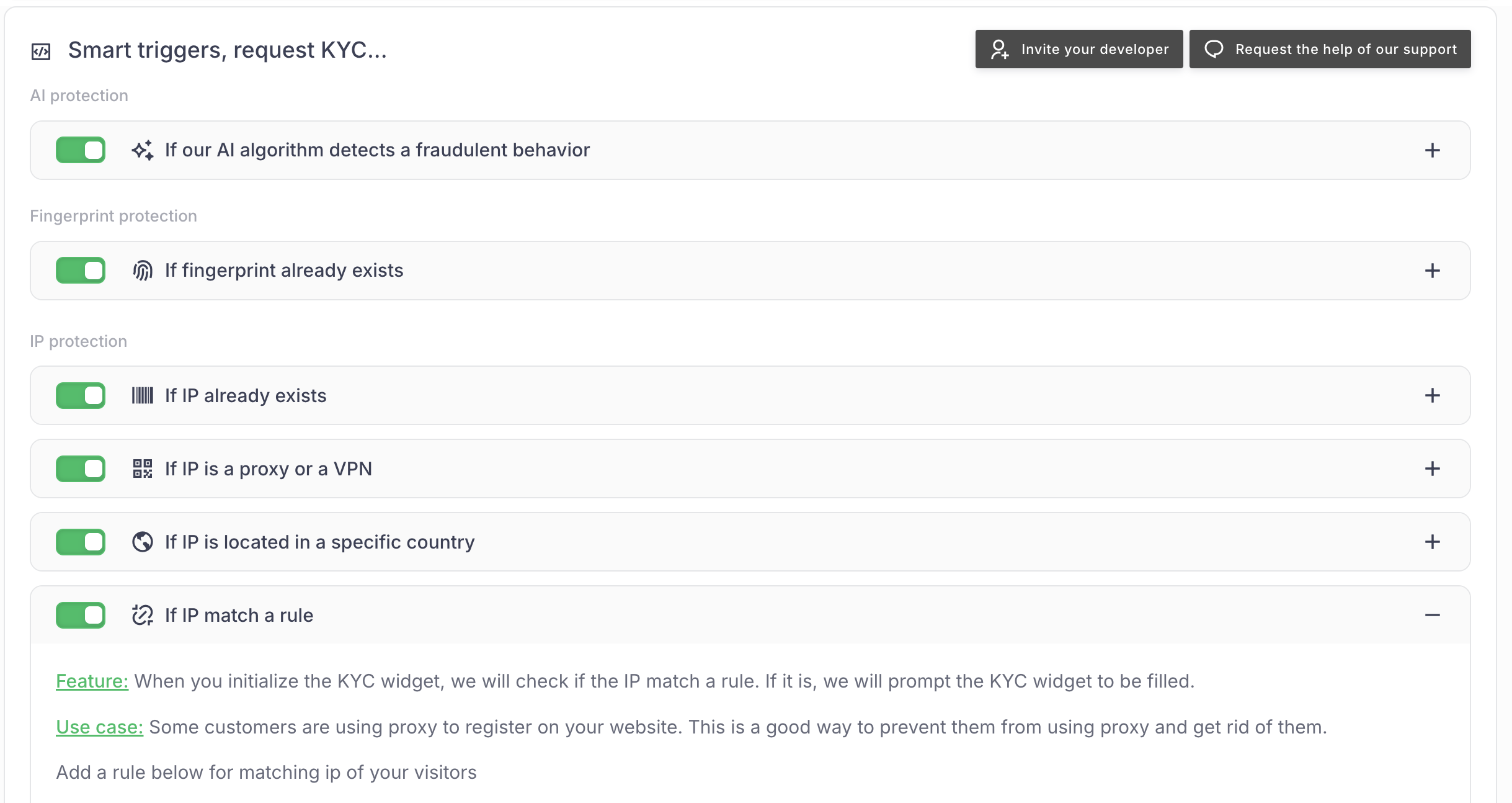
Advanced Triggers
Smart automation that protects your platform from fraud.
Fingerprint Detection
Automatically detect duplicate registrations using unique visitor fingerprints.
IP & Location Rules
Trigger KYC based on IP location, proxy/VPN detection, and country restrictions.
Bot Detection
Identify automated behavior patterns and suspicious user interactions.
Email Validation
Detect temporary mailboxes and suspicious email patterns automatically.
Advanced fraud detection and automated triggers
Our AI-powered system automatically detects suspicious behavior and triggers KYC verification when needed, protecting your platform from fraud while maintaining a seamless user experience.
95%
fraud detection accuracy
85%
reduction in fake accounts
60 seconds
average verification time
"The KYC widget has been a game-changer for our platform. Automated fraud detection has reduced our fake account creation by 85% while maintaining a smooth user experience. The AI triggers are incredibly accurate and save us hours of manual review every day."
AI-powered fraud detection
Our advanced AI algorithm automatically detects suspicious behavior patterns and triggers KYC verification to prevent fraudulent activities on your platform.
Smart fingerprint tracking
Automatically detect duplicate registrations and prevent fake accounts by tracking unique visitor fingerprints across your platform.
Geographic risk assessment
Set up automatic KYC triggers based on specific countries or regions to manage risk according to your business requirements.
Proxy and VPN detection
Identify users hiding behind proxies or VPNs and automatically trigger KYC verification to ensure legitimate user registration.




Ready to protect your website?
Install our widget on your website in minutes
Get Started



